Cybersecurity
Advanced protection against threats
At Expandlogix, we help organisations strengthen their security for a digital age. Our Cyber Security Solutions provide organisations with the visibility and velocity they need to respond to advanced threats at the core in the datacenter and at the edge in the workplace. We exploit analytics. We deploy next-generation defences. And we unify event management.
Why Expandlogix?
- Accreditations with all key vendors
- 20+ certifications in security solutions, including firewalls and DDoS protection
- Cyber Defence Center helps organisations defend smarter and react faster We cover every stage of the cyber security cycle, from protection and detection to reaction and prevention.
A holistic approach
By taking a holistic approach across the workplace, the network, the datacenter and the cloud, ExpandLogix safeguards business continuity and critical infrastructures.
Our Cyber Security Services provide the advanced protection and intelligence needed to stay one step ahead of the known and the unknown risks in information technology.
From evaluating new cyber security tools and undertaking vulnerability assessments to providing compliance reports, ExpnadLogix minimizes costs and complexity while saving time and maximizing revenue for the organization.
Proactive not Reactive
ExpandLogix’s Cybersecurity services identify and close the gaps that expose the business and its users to IT risk. We reduce disruption. We enable digitisation. We make security proactive.
Internal traffic has to be protected too
Many companies concentrate mostly on the perimeter firewall and so called north-south traffic when devising plans to protect themselves from cyber attacks. However, once a perpetrator gets into the network, the damages can imense. To stop attacks from within and without, smart cyber security solutions are needed that can do much more than filter out spam and malware.
To ensure that your business vital data is protected, ExpandLogix offers a range comprehensive of IT security solutions. We provide full protection, combining technical security with information security. An integrated security strategy is the best way to counter malware, data spying, and data theft. Our certified experts will provide you with reliable, future-ready strategies—guaranteed.
We provide the following solutions for technical security and information security:
Technical security.
- Data security: E-mail encryption, data loss prevention, PKI, authentication
- Endpoint security: Antivirus and anti-malware solutions, personal firewalls and host IPS, hard drive encryption
- Network security: 802.1X-based LAN and wireless security, IP address management strategies
- Internet security: Firewalls, VPN, IPS, secure access
Information security.
- Data protection: Consulting, audits, training, external data protection officer, assessor
- Data security: Assessments, security strategies, certification preparation
- Legal compliance consulting: Liability, employment contracts, works council agreements, compliance, IT law
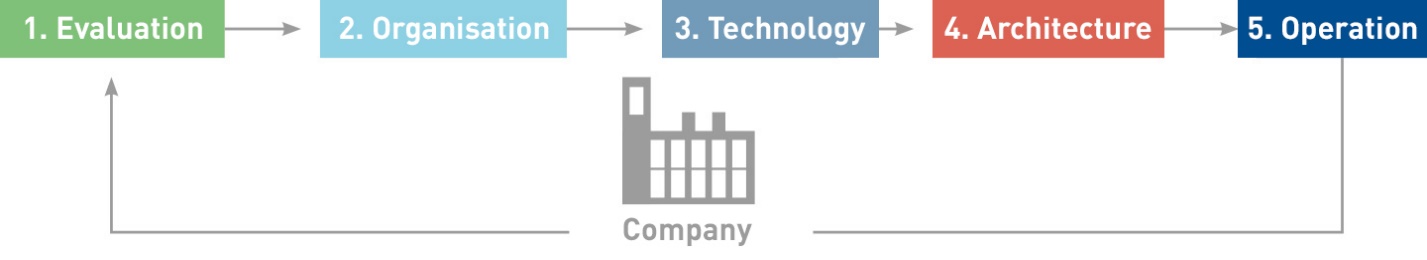
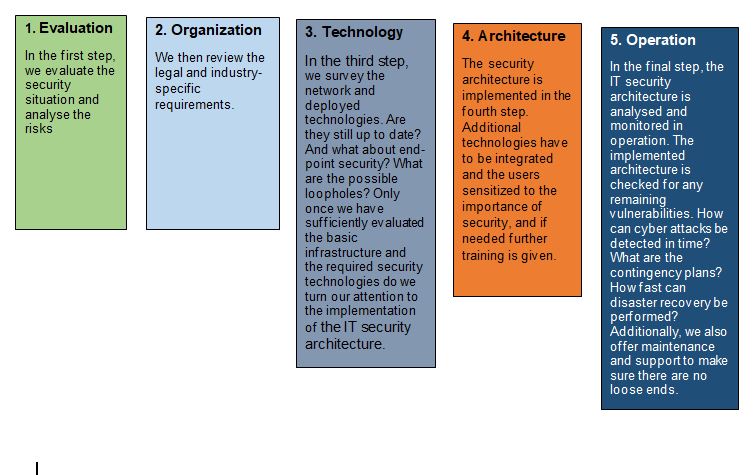
A secure solution: the IT security architecture.
Effective IT security requires a holistic approach. It’s the only way to guarantee that security loopholes are closed. Our IT security architecture consists of a five-step process.
The ExpandLogix Security portfolio
Endpoint Security
Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns. Endpoint security systems protect these endpoints on a network or in the cloud from cybersecurity threats. Endpoint security has evolved from traditional antivirus software to providing comprehensive protection from sophisticated malware and evolving zero-day threats.
Organizations of all sizes are at risk from nation-states, hacktivists, organized crime, and malicious and accidental insider threats. Endpoint security is often seen as cybersecurity's frontline, and represents one of the first places organizations look to secure their enterprise networks.
As the volume and sophistication of cybersecurity threats have steadily grown, so has the need for more advanced endpoint security solutions. Today’s endpoint protection systems are designed to quickly detect, analyze, block, and contain attacks in progress. To do this, they need to collaborate with each other and with other security technologies to give administrators visibility into advanced threats to speed detection and remediation response times.

E-mail Security
Email security includes the techniques and technologies used to protect email accounts and communications. Email, which is an organization’s largest attack surface, is the primary target of phishing attacks and can be used to spread malware.
A secure email gateway (SEG) acts as a firewall between outsiders and users’ email accounts. It protects both inbound and outbound communications using a message transfer agent (MTA) or an application programming interface (API) to scan email and enforce security policies. An SEG checks emails for spam, malware, and other elements designated by your IT team.
Our Solutions can protect against threats such as phishing, spam, and various types of malware by scanning the contents of emails. It can also detect attempts to leak data from your system and apply encryption to prevent your messages from being read by eavesdroppers.

Network Security
Network Security protects your network and data from breaches, intrusions and other threats. This is a vast and overarching term that describes hardware and software solutions as well as processes or rules and configurations relating to network use, accessibility, and overall threat protection.
Network Security involves access control, virus and antivirus software, application security, network analytics, types of network-related security (endpoint, web, wireless), firewalls, VPN encryption and more.
Cloud Security
Cloud security, also known as cloud computing security, consists of a set of policies, controls, procedures and technologies that work together to protect cloud-based systems, data, and infrastructure. These security measures are configured to protect cloud data, support regulatory compliance and protect customers' privacy as well as setting authentication rules for individual users and devices. From authenticating access to filtering traffic, cloud security can be configured to the exact needs of the Business. And because these rules can be configured and managed in one place, administration overheads are reduced and IT teams empowered to focus on other areas of the Business.
The way cloud security is delivered will depend on the individual cloud provider or the cloud security solutions in place. However, implementation of cloud security processes should be a joint responsibility between the Business owner and solution provider.
Gateway Security
Gateway security protects users from the multiple threats at modern web and email gateways on all devices – from smartphones to laptops and desktop computers. It makes Business-critical web and email services safer, reducing the risks of today’s increasingly connected world.
We cover both web and email security, and provide:
- Hybrid cloud mail and web gateway services incorporating cloud application control
- Integration with Data Loss/Leakage Prevention (DLP) Services
- Application-aware content filtering
- Advanced ‘zero-day’ threat detection capability with global threat intelligence feeds
- Enhanced management of Office 365 and Gmail
Identity & Access Management Security
An Identity and Access Management (IAM) system defines and manages user identities and access permissions. Users of IAM include customers (customer identity management) and employees (employee identity management). With IAM technologies, IT managers can ensure that users are who they say they are (authentication) and that users access the applications and resources they have permission to use (authorization).
4 Key Benefits of Identity and Access Management Systems
- Eliminating weak passwords—research shows over 80% of data breaches are caused by stolen, default, or weak passwords. IAM systems enforce best practices in credential management, and can practically eliminate the risk that users will use weak or default passwords. They also ensure users frequently change passwords.
- Mitigating insider threats—a growing number of breaches is caused by insiders. IAM can limit the damage caused by malicious insiders, by ensuring users only have access to the systems they work with, and cannot escalate privileges without supervision.
- Advanced tracking of anomalies—modern IAM solutions go beyond simple credential management, and include technologies such as machine learning, artificial intelligence, and risk-based authentication, to identify and block anomalous activity.
- Multi-factor security—IAM solutions help enterprises progress from two-factor to three-factor authentication, using capabilities like iris scanning, fingerprint sensors, and face recognition.

Security Management & Control
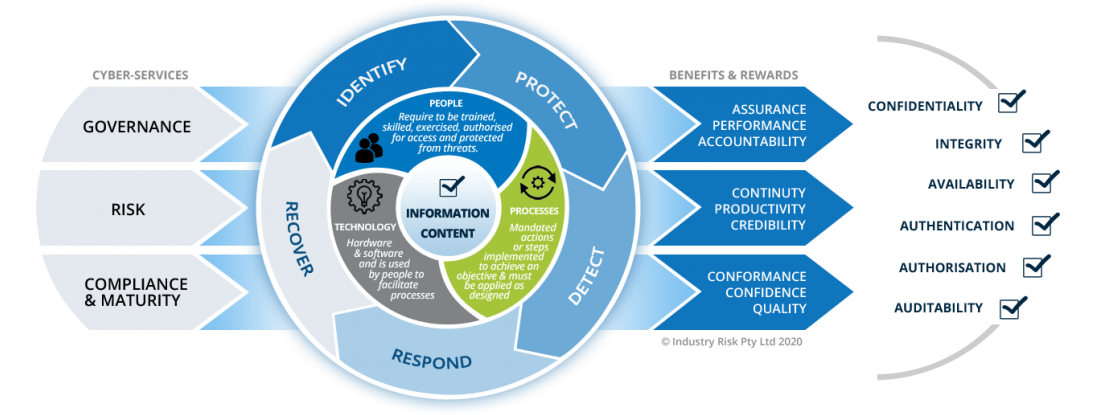
Management security is the overall design of your controls. Sometimes referred to as administrative controls, these provide the guidance, rules, and procedures for implementing a security environment.
What is Operational Security?
Operational Security is the effectiveness of your controls. Sometimes referred to as technical controls, these include access controls, authentication, and security topologies applied to networks, systems, and applications.
What is Physical Security?
Physical security is the protection of personnel, data, hardware, etc., from physical threats that could harm, damage, or disrupt Business operations or impact the confidentiality, integrity, or availability of systems and/or data.
ExpandLogix’s vendor independence enables us to deliver best of breed solutions for our customers. By understanding your Business requirements and drawing on our expertise of delivering transformation across Core infrastructure and Edge solutions we are able to make informed recommendations around the most suitable technologies to meet your Business needs.



